- Cointelegraph’s frontend was compromised by malicious ad scripts, showing a fake CTG token giveaway designed to drain user wallets.
- Security firm Scam Sniffer traced the breach to a third-party ad provider, mirroring a similar incident that recently targeted CoinMarketCap.
- The CTG token is fake and unlisted, but the scam’s polished interface fooled users into connecting wallets, risking total fund loss.
A weekend security incident on Cointelegraph has renewed industry worries about a fast-growing malware tactic that hides malicious code inside advertising scripts on reputable crypto sites. The episode mirrors a recent compromise at CoinMarketCap and highlights how attackers now favor front-end ad vectors over traditional email phishing.
Fake “CTG Airdrop” lures readers with bogus $5K prize
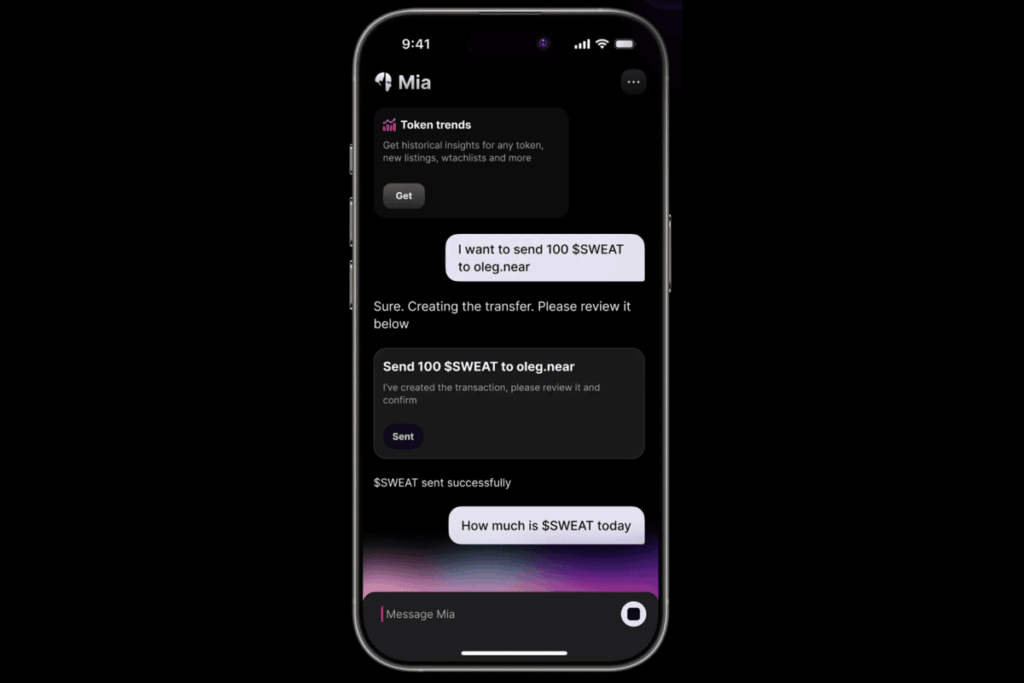
Visitors to Cointelegraph were greeted by a convincing pop-up that claimed they had randomly won 50,000 “CTG” tokens worth more than $5,000. The promotion looked legitimate: it used Cointelegraph branding, a countdown timer, and a wallet-connect prompt hallmarks of genuine token launches. Every element, however, was fabricated.
Blockchain security outfit Scam Sniffer quickly sounded the alarm on X, warning that Cointelegraph’s front end had been tampered with. Screenshots posted by the firm showed injected JavaScript designed to trick users into approving wallet transactions that would silently empty their accounts.
Newsletter
Get weekly updates on the newest crypto stories, case studies and tips right in your mailbox.
Cointelegraph confirmed the breach shortly after the alert, advising readers to avoid the pop-up and stressing that it has never issued a CTG token or conducted any initial coin offering. Engineers began removing the malicious code and reassured users that core site infrastructure remained intact.
Compromised Ad script identified as infection source
According to Scam Sniffer’s forensic analysis, the rogue code did not originate from Cointelegraph’s servers but from an external advertising script supplied by a third-party partner. The infected file masqueraded as routine ad tech while harboring wallet-draining functions.
This method is gaining favor among threat actors because it leverages trust in well-known domains. Once embedded, the code can display polished scams directly inside a site’s user interface, bypassing email filters and social-media warnings that have made classic phishing less effective.
A nearly identical exploit appeared on CoinMarketCap earlier in the month, where attackers slipped a malicious link into a promotional banner. That breach also traced back to external code rather than CoinMarketCap’s own systems.
Non-existent CTG token flags instant red alert
Security analysts note that CTG is not listed on CoinMarketCap, CoinGecko, or any major blockchain explorer, an obvious red flag to seasoned traders. Newcomers, however, may still fall for the ruse, mistaking the professional design for proof of authenticity.
The fake interface even labeled the process “secure,” “instant,” and “verified,” further lowering users’ guard. Once a wallet connected, hidden scripts could issue approval transactions, granting the attacker unlimited spending rights and paving the way for a full asset drain.
Security experts are urging platforms to sandbox third-party scripts, conduct deeper audits of ad suppliers, and adopt real-time monitoring to detect anomalous front-end changes. Until such measures become standard, users are advised to treat any sudden wallet-connect prompt even on trusted sites with extreme caution.