Mandiant, which is part of Google Cloud, has been following the suspected North Korean fraudsters since 2018. But since November 2025, AI has made it easier for them to launch more attacks.
Threat actors linked to North Korea are ramping up social engineering attacks against cryptocurrency and fintech organisations by using new malware that is meant to steal sensitive data and digital assets.
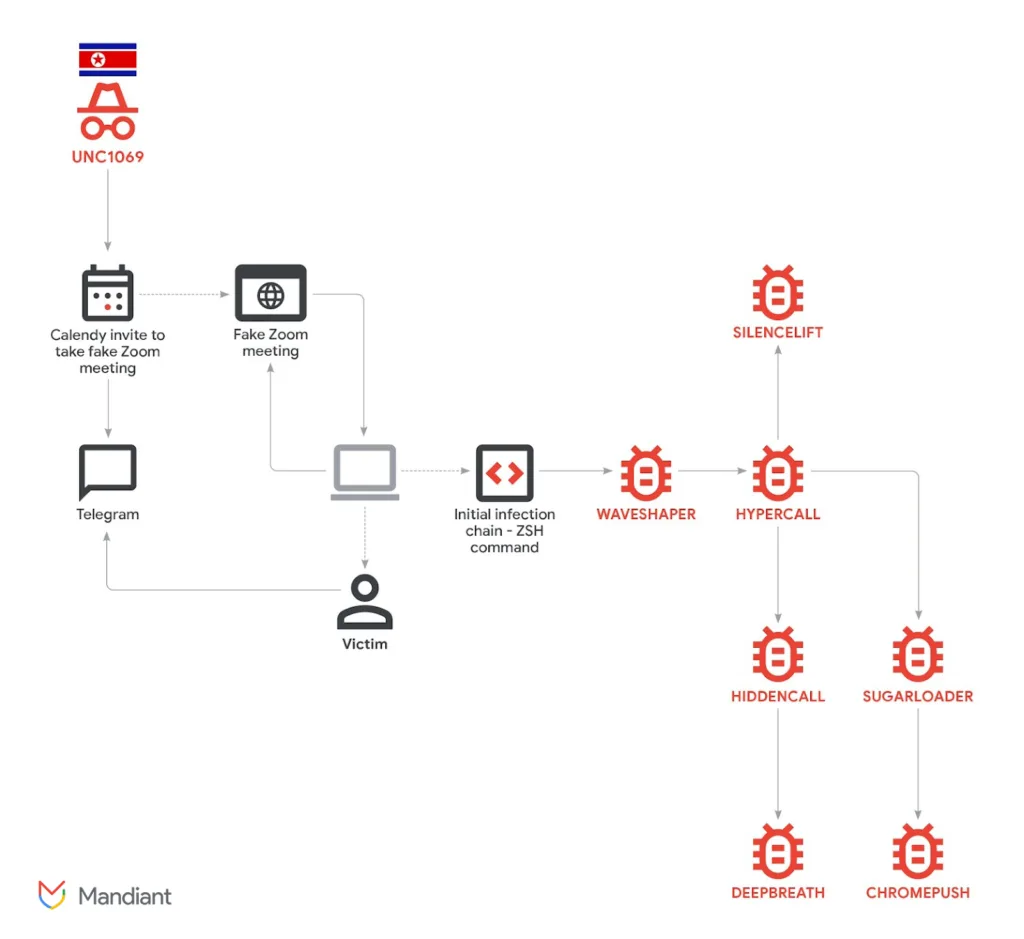
According to a report from Mandiant, a US cybersecurity company that works for Google Cloud, a threat group known as UNC1069 used seven types of malware in a recent campaign to steal and exfiltrate victim data.
Source: Mandiant/Google Cloud
New malware families deployed in targeted intrusions
The campaign included social engineering tactics that involved hacked Telegram accounts and bogus Zoom meetings with deepfake videos made by AI tools.
The study says, “This investigation revealed a tailored intrusion resulting in the deployment of seven unique malware families, including a new set of tools designed to capture host and victim data: SILENCELIFT, DEEPBREATH, and CHROMEPUSH.”
Mandiant says that the group’s activities have grown, and they are now mostly going after crypto startups, software engineers, and venture capital firms.
The malware had two new, advanced data-mining viruses called CHROMEPUSH and DEEPBREATH. They are made to get around important parts of the operating system and get to personal data.
Mandiant has been keeping an eye on the threat actor with “suspected” North Korean ties since 2018. However, thanks to advances in AI, the bad actor was able to grow its operations and include “AI-enabled lures in active operations” for the first time in November 2025, according to a report from the Google Threat Intelligence Group at the time.
ClickFix technique used to compromise crypto founders
According to Mandiant, attackers exploited a hacked Telegram account belonging to a crypto entrepreneur to start a conversation in one case. The attacker invited the victim to a Zoom conference where they pretended to be having trouble with the audio.
In a ClickFix attack, the attacker told the victim to run troubleshooting commands on their machine to remedy the fake audio problem.
Mandiant said that the troubleshooting commands included a secret single instruction that started the infection chain.
People who are connected to North Korea have been a constant threat to both crypto investors and Web3-native businesses.
The Lazarus Group was connected to the $1.4 billion hack of Bybit, which was one of the biggest crypto thefts ever, earlier that year.



