- Arizona woman sentenced to 8.5 years for helping North Korean hackers infiltrate over 300 U.S. crypto and tech companies.
- Scheme generated $17M+ in illicit gains using stolen identities, with operatives posing as U.S.-based remote IT workers.
- One of the largest DPRK cyberfraud cases ever, raising serious compliance concerns for firms unknowingly hiring sanctioned developers.
An Arizona woman, Christina Marie Chapman, has been sentenced to 102 months (8.5 years) in federal prison after pleading guilty to wire fraud conspiracy, aggravated identity theft, and money laundering. Chapman played a central role in a North Korean scheme that allowed operatives to obtain remote jobs at more than 300 U.S. cryptocurrency and tech companies using stolen or falsified identities.
The U.S. Attorney’s Office for the District of Columbia announced that Chapman facilitated the infiltration of 309 U.S. businesses and two international companies, generating over $17 million in unlawful revenue. Her sentencing also includes three years of supervised release, forfeiture of $284,000, and $177,000 in restitution.
This case is now considered one of the largest IT infiltration operations by the Democratic People’s Republic of Korea (DPRK) charged by U.S. authorities. The Department of Justice revealed that at least 68 U.S. identities were compromised in the operation.
Newsletter
Get weekly updates on the newest crypto stories, case studies and tips right in your mailbox.
DPRK’s expanding reach
The ruling highlights the growing threat of North Korean cyber actors, who continue to infiltrate global tech firms under the guise of freelance developers. Recent reports mention similar tactics used to infiltrate both a U.S. crypto startup and a Serbian token firm, stealing over $900,000.
Earlier this month, the U.S. Treasury sanctioned two individuals and four entities believed to be part of a DPRK-run remote work network. The illegally earned crypto is believed to be funding North Korea’s weapons of mass destruction program.
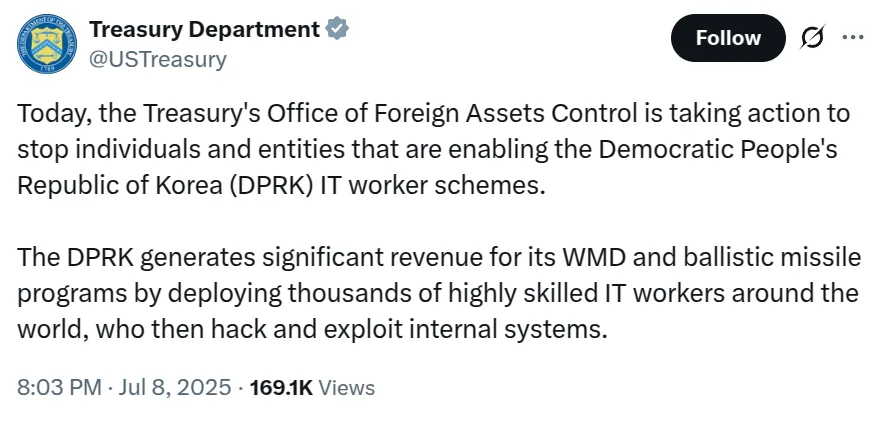
Source: Treasury Department
Cybersecurity firms like Google’s Threat Intelligence Group and legal experts are now urging U.S. companies to improve identity verification protocols to avoid unknowingly violating U.S. sanctions laws. Under OFAC’s strict liability regime, even unintentional transactions with sanctioned individuals may result in civil or criminal penalties.