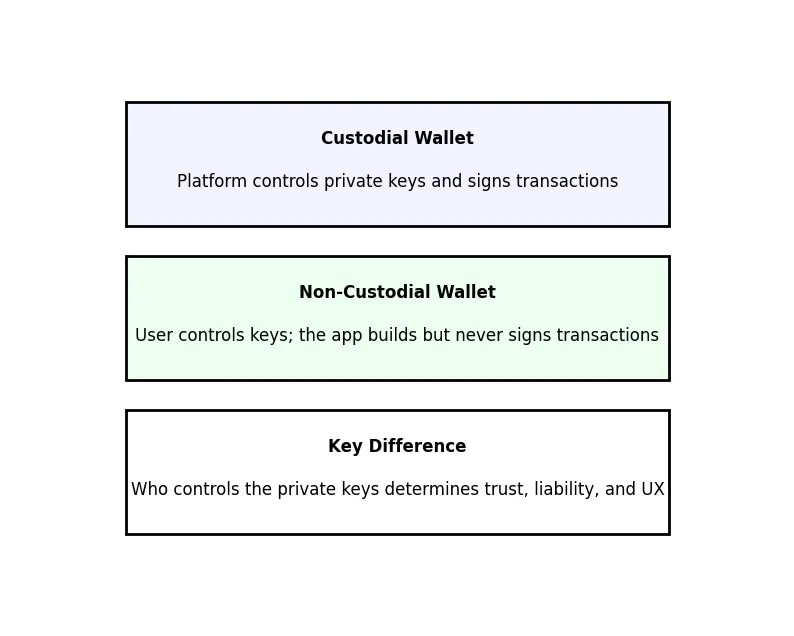
In a custodian wallet the private keys are not stored examples by the user instead the platform manages them. This architecture is basically like a normal financial product: the users log in with their phone number, email, or social media and the platform does all the cryptographic transactions in the background. The firm can support account restoration, compliance checks, fraud detection, withdrawal monitoring, and hassle-free user experiences without revealing the technicalities of blockchain since it has the keys. The company takes on legal responsibility for the protection of the assets, security risk, and regulatory obligations in return.
Non-custodial wallets do the opposite of what custodial wallets do. The user has the private keys which are usually not given away if the user has such a secure enclave, MPC scheme, or seed phrase. As the platform does not possess the keys, it can neither recover accounts nor freeze funds or revert errors. This approach is appealing to the crypto-native users and is in line with the decentralization philosophy. It reduces the risk of a centralized honeypot and lowers the company’s regulatory load but it does so at the cost of passing security and UX complexity on to the user. If a user loses possession of their keys the assets are gone.
Evaluation using typical product and strategy criteria
Seamless onboarding, activation and retention are usually the main users’ concerns with custodial wallets and so, it works best in such cases. The newcomers or the web2 users are not ready to deal with blockchain gas rules or seed phrases; they prefer logins similar to those used in modern-day apps, i.e., simple and straightforward. Custodial model creates the possibility of instant access, fast conversions, and more sophisticated control over the product.The non-custodial model is justified when user control, decentralization, and trustless transactions are the priorities.
Technically savvy users often want to have power over their assets, visibility on-chain transactions and the assurance that the platform will not block them or confiscate their money.Another decisive factor is compliance. The custodial model may trigger regulations such as KYC, AML, custody licensing, and specific regional requirements. Though a non-custodial approach cannot claim to be free from all obligations, it certainly lessens many of them, especially when the service it provides includes facilitating transactions, swaps or contract interactions. The two models also differ in terms of security and liability.
A custodial system concentrates risk because any security breach might have severe consequences, and the platform has to secure access to the system, infrastructure, and private keys internally. A non-custodial system decentralizes these risks, but the platform still has to provide very strong user training and user-friendly interfaces to avoid accidental loss or mistakenly signed transactions. From the business viewpoint, custodial wallets are more favorable as the platform controls the flows and is able to optimize routing, batching, spreads, and yield products which means more monetization opportunities. On the other hand, transparent on-chain interactions, which are the ones usually generating income through routing fees, subscription services or value-added prod
Practical feature models you can build
All cryptographic control is secure and centralized in the case of a pure custodial wallet platform. The user experience is similar to that of banking or trading apps, with a simple login and a single view of all possessions. The company provides a seamless user experience that hides the complexity of blockchain technology and takes on-chain actions for the user. This method works well for the mass market consumers who are not ready yet to deal with compliance, security, and custody issues.
The management of assets is totally in the hands of the user with a pure non-custodial wallet. The platform facilitates the interaction by guiding users to make keys, connecting existing wallets, or using contract-based or MPC-based systems. The user always approves transactions on his/her device first. Rather than asset control, the platform focuses on tooling, education, and safe UX patterns. This model is the most compatible with decentralization for crypto-native users. The hybrid approach is the one that takes advantage of both.
The platform can provide a self-custody mode that is optional and a custodial environment that is gentle to newcomers by default. Another option involves the use of MPC wallets or non-custodial smart contracts which are perceived as custodial by the user due to the more convenient recovery flows but the platform is never in possession of the private key. By giving custody to a licensed third-party provider, a third approach allows the platform to offer custodial UX without incurring the entire regulatory burden. Hybrid designs are often the ones selected because they cater to both beginners requiring simplicity and experts craving control. They also make a gradual evolution possible: Product could initially be developed with a custodial flow for quick use.
You can make an internal decision using a decision template.
If you wish to apply your own standards, you could connect each element such as target audience, regulatory comfort, monetization strategy, security capability, and support expectations to a custodial model or to a non-custodial one. By assigning a value to each factor based on its significance to your product, you will be in a position to select the strategy that aligns with your strategic objectives the most. It will ultimately result in a fair comparison, which sometimes uncovers the best solution as a hybrid one.