Encrypted AI Audit Trails establish a protected system which enables both verification and documentation of AI-driven decision-making processes. The feature is used in situations where artificial intelligence systems determine financial results and compliance decisions and risk assessment. The system approves all AI decision processes because it enables users to recreate and verify decisions without sharing protected information and without using changeable system records.
Purpose and rationale
As AI systems become embedded in high-stakes decision-making, existing logging methods need to be replaced because they fail to meet current requirements. The system permit entry of changes to centralized logs which can be deleted and disputed while the logs themselves protect nothing through cryptographic methods. The Encrypted AI Audit Trails system solves this issue through its design of an unchangeable proof system that records decision times and decision model usage and decision-making policy while keeping all data private.
Scope of application
The feature applies to any AI system that produces automated outputs or recommendations with financial operational or regulatory effects. The system includes risk scoring models and fraud detection engines and trading and execution systems and portfolio management tools and compliance screening processes. The system design allows model-agnostic operation which supports both deterministic AI systems and probabilistic AI systems.
Decision trace capture
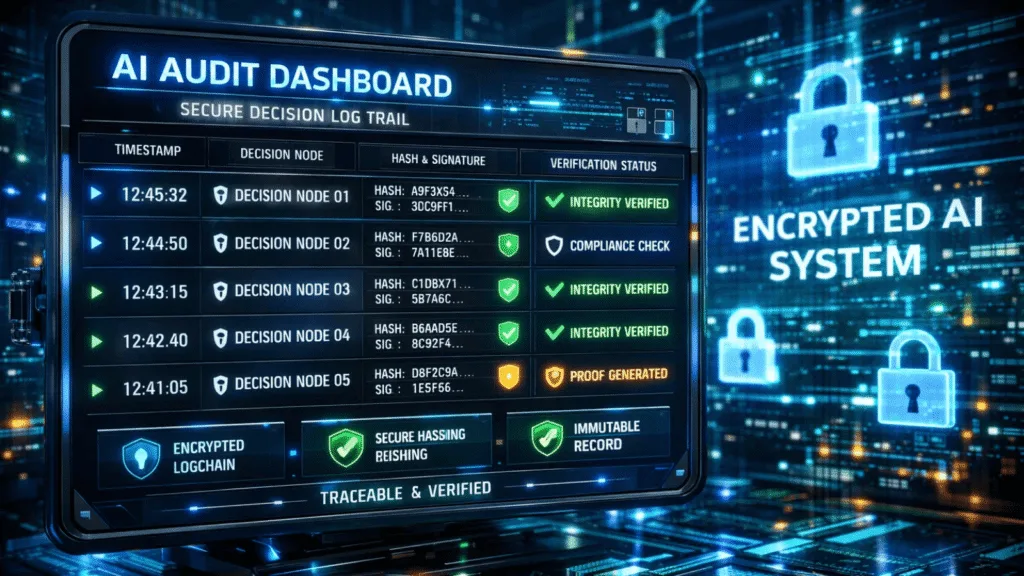
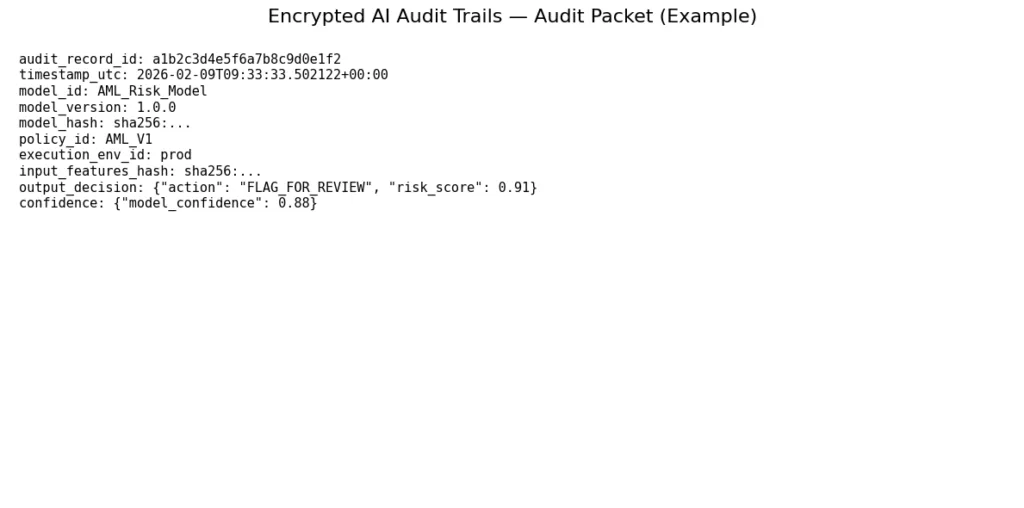
The AI system creates structured decision traces which contain essential elements needed to demonstrate decision validity. The trace includes the identity and version of the model, the execution timestamp, a cryptographic representation of the inputs, the output decision or action, associated confidence metrics, and the policy context governing execution. The trace is created to enable audit purposes through its design which ensures predictable and repeatable results.
Privacy and encryption model
The system design uses privacy protection as its main design principle. The system does not keep any raw data which includes input data output data and processing data in its on-chain storage. The system uses strong symmetric encryption to protect its entire decision-making process which remains stored in an off-site secure facility. The system records only a cryptographic hash of the protected data together with non-confidential metadata on the blockchain. The system maintains security through its confidential data protection system while enabling verification of information.
Blockchain anchoring layer
The blockchain serves as an unchangeable system which provides both time-stamping and identity verification solutions. The moment of execution results in each encrypted decision trace being converted into a hash which gets stored on the blockchain. The on-chain record contains no business-sensitive data and is designed to minimize storage and execution costs. The anchoring process establishes a security measure which prevents any unauthorized changes to decision records.
Off-chain storage architecture
Secure off-chain repositories maintain encrypted decision traces which include enterprise vaults and encrypted object storage and distributed storage networks. The audit mechanism remains independent from storage systems which enables organizations to choose infrastructure that matches their security needs and jurisdictional requirements and operational demands.
Audit and verification process
The authorized parties request access to decision records after they start an audit. The controlled environment retrieves and decrypts the encrypted trace after it receives approval. The system performs a new cryptographic hash calculation which it verifies by comparing the result to the on-chain record. The AI decision record achieves a successful match which verifies both its authenticity and its integrity.
Access control and governance
People can access audit records through two control systems which require them to have specific roles and follow established policies. The system records all access attempts which creates a second audit trail that enables monitoring and accountability. Organizations control permission access through time restrictions and scope boundaries and role-based requirements which restrict sensitive information access to authorized individuals who meet predefined conditions.
Compliance and regulatory alignment
Encrypted AI Audit Trails enable organizations to meet both upcoming AI governance requirements and current financial regulation standards. The feature provides auditable evidence of model usage, decision consistency, and policy adherence without disclosing proprietary data. Organizations can use cryptographic evidence to answer regulatory inquiries instead of relying on manual verification methods.
Implementation phases
The first phase of the project implements three systems that protect encrypted decision-making process and use blockchain technology for verification and track internal audit activities. The following project stages will introduce new security systems that use advanced cryptographic methods and automated access systems for regulatory purposes and cross-chain anchoring to improve system resilience and interoperability.
Strategic value
The Encrypted AI Audit Trails system creates unchangeable and verifiable AI decision processes which reduce legal liabilities and build institutional credibility while providing a basis for controlled AI operations. The feature positions AI systems as accountable infrastructure rather than opaque tools, which enables organizations to maintain their technological performance while complying with extended regulatory requirements and institutional demands.