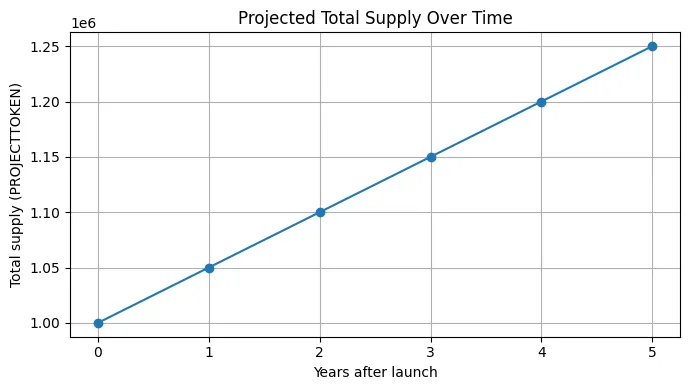
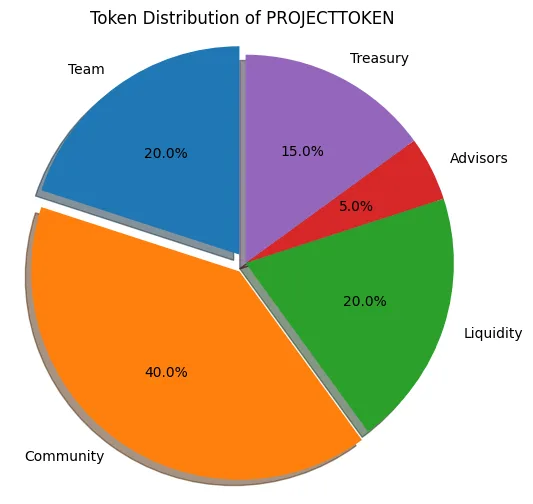
In essence, an ERC-20 token is a deterministic state machine that operates on the EVM and is in charge of monitoring balances, permissions, metadata, and transfer logic. The basic ERC-20 interface is very straightforward, but in actual production settings, tokens frequently need extra features like optional minting, controlled burning, treasury-based fee routing, role-based access control, stopping for emergency conditions, and other behavioral modifications. The design employed here simulates a modular token that maintains complete compatibility with the ERC-20 standard and the accompanying tooling environment while exhibiting predictable behavior under stress.
Real engineering teams typically use Hardhat or Foundry for testing, static analysis, deployment automation, and continuous integration workflows, even if this version can be distributed using Remix for demonstration. In order to allow it to be dropped into any professional development environment without change, the code below purposefully avoids experimental features.
Architectural foundations
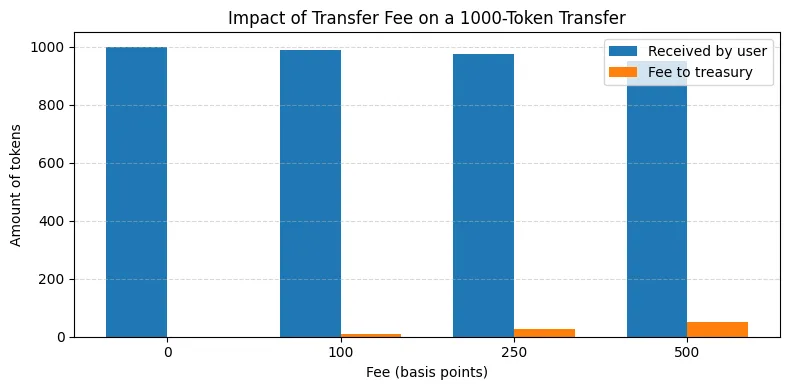
With the addition of burnability, pausing, administrative control, and a basis-points-based fee structure that is routed to a specific treasury address, the token shown here exposes a traditional ERC-20 interface. Every state change pertaining to token movement is handled by a single, predictable process thanks to the architecture’s single override of _transfer. To prevent recursion and double-charging, fee exemptions are applied to transactions in which the Treasury takes part.
To ensure that administrative control cannot be abused to the point where the token’s economic viability is destroyed, a maximum fee constraint is hard-coded. Once a threat or integration issue has been fixed, the contract owner can unpause the system using the pause functionality, which functions as a global state lock and prevents any transfer, mint, or burn activities while permitting read-only interaction.
Internal mechanics and engineering rationale
When the contract is halted, the pausing mechanism uses the _beforeTokenTransfer hook to guarantee that any state-changing ERC-20 activities stop right away. This guarantees that under emergency situations, the system cannot undergo partial state transitions. Instead of employing a global pause switch, the logic would need to be divided into distinct roles if your architecture calls for mints or burns to continue during paused mode.
Basis points are used in the charge system to prevent floating numerical uncertainty. Basis points prevent problems with multiplication and division rounding inconsistencies and provide deterministic behavior in all settings. The coin can maintain full ERC-20 compliance while adding predictable modular extension behavior thanks to the fee logic included under _transfer. In order to prevent infinite loops and recursive charging, transfers using the Treasury address skip fee application.
Strict invariants are adhered to by the state machine. Only when minting or burning takes place does the overall supply change. Any transfer’s total movement is equal to the sum of the fee and the transferred net amount. Although read visibility and administrative calls are not blocked, the stopped state stops any irrevocable state changes from happening.
Deployment flow
Clicking “Deploy” in Remix is only one part of a production deployment strategy. Setting up environment variables for constructor parameters and executing complete unit and fuzz tests are the first steps in the professional workflow. To find harmful state mutations, storage architecture problems, and reentrancy patterns, static analysis utilizing Slither and MythX should be carried out. After they are satisfied, deployment scripts in Foundry or Hardhat manage automated Etherscan verification, constructor parameter injection, and bytecode publication.
Tokenomics modeling should be used to determine constructor values for supply and fee parameters rather than making do on the fly during deployment. Before moving to the mainnet, a complete cycle of state transition validation, fee logic consistency checking, and treasury transfer tests must be completed after deployment to a testnet. Broadcasting the signed transaction, exporting ABI files for frontend and backend services, confirming the implementation on Etherscan, and transferring ownership to a multisignature wallet are all part of the final deployment process.
Security and production considerations
In a practical deployment, the owner should never be an externally owned account (EOA) due to the importance of administrative rights in this architecture. The administrative tasks should be managed via a multisignature wallet. To make reasoning about state and storage structure easier, this contract is purposefully non-upgradeable. The design must change to a UUPS proxy architecture with suitable storage gaps and initializer patterns if upgradeability is necessary.
Although it offers a robust emergency control surface, the pause mechanism needs to be handled cautiously to prevent governance abuse. Decentralization-focused projects frequently limit pause functionality or demand multisig approval. By prohibiting excessive fee manipulation that might be used to capture user funds, the transfer fee cap upholds economic safety.
Extensibility of this architecture
More sophisticated systems like staking vaults, time-locked vesting, governance voting, bonding curves, rebasing supply methods, liquidity mining systems, payment streaming, or gasless signature approvals via EIP-2612 can be built upon the supplied contract. These expansions are already supported without architectural conflict by the allowance mechanism and transfer pipeline.
Production readiness
Make sure that thorough testing has been done before deploying any token to the mainnet. This entails fuzzing random address interactions, checking invariants, executing whole simulation frameworks, verifying code coverage levels, conducting audits, and establishing that parameters like ownership flow, fee structure, and treasury address correspond to the final economic design.