What it is
ZK-ID Vault™ is a zero-knowledge identity infrastructure that allows users to prove credentials without exposing personal data. Instead of uploading passports, utility bills, or full KYC records to every new platform, users generate cryptographic proofs that confirm eligibility while keeping the underlying information hidden. The system verifies statements, not identities.
A platform does not need to know your exact birthdate to confirm you are over 18. It does not need to see your passport to confirm you passed KYC with an approved provider. It only needs proof that the condition is satisfied.This transforms identity from a data-sharing process into a verification process.
Why this matters now
The regulatory pressure which affects both crypto and fintech operations has reached its highest point yet. The exchange operators need to implement geographical access limits which reflect their jurisdictional boundaries. The DeFi protocols are testing their compliance systems through various experimental methods. The authorities have started to conduct more thorough investigations into stablecoin issuers. Users now show less willingness to share their confidential information after each instance.
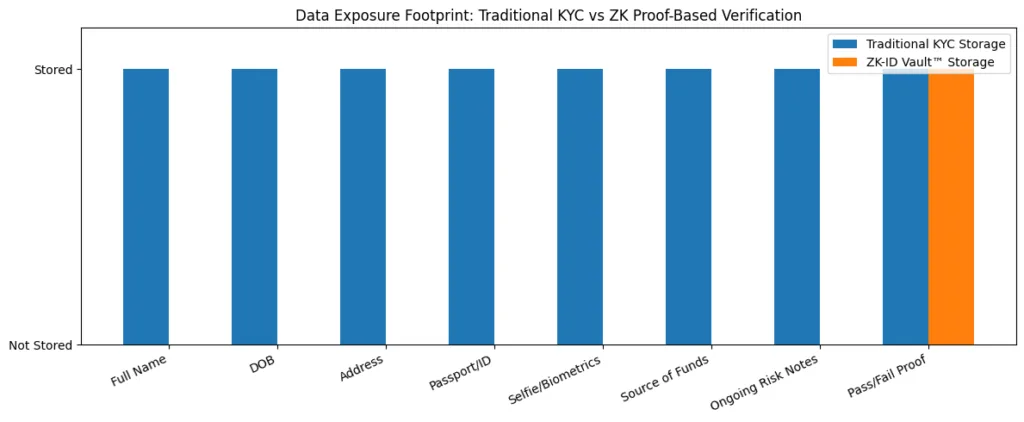
The current system requires platforms to handle extensive personal data which results in operational risks and legal liabilities and security breach risks. The identity verification system based on zero-knowledge proof technology creates a new system design. Users keep their passwords and share their authentication proof as needed instead of keeping their personal information on multiple websites. Organizations can meet their compliance obligations because they can implement security measures without storing confidential data in centralized locations. Privacy and regulation no longer sit in opposition.
How it works
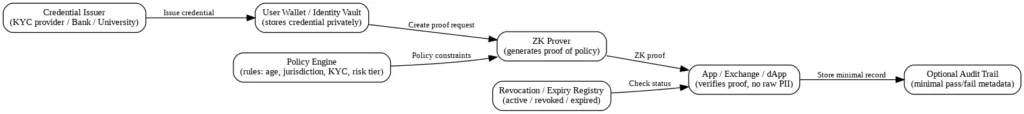
The system begins with a credential issuer. Any approved authority which can issue attestations serves as a credential issuer which includes KYC providers and financial institutions and universities. The issuer delivers a cryptographic credential after users complete their verification process. The user stores the credential in a secure wallet which functions as an identity vault. The platform needs authentication but it does not need to see any documents. The platform needs to detect proof which complies with its established policy rule.
The user creates a zero-knowledge proof which demonstrates that he meets the necessary requirements. The platform uses the proof to verify its contents without needing to see the actual data. The result shows that all policy requirements have been met while protecting personal information from exposure. The system uses revocation and expiration mechanisms to maintain credential validity until the user status has been confirmed as active. The validation process for proofs will fail when a credential has been revoked or expired.
Product experience
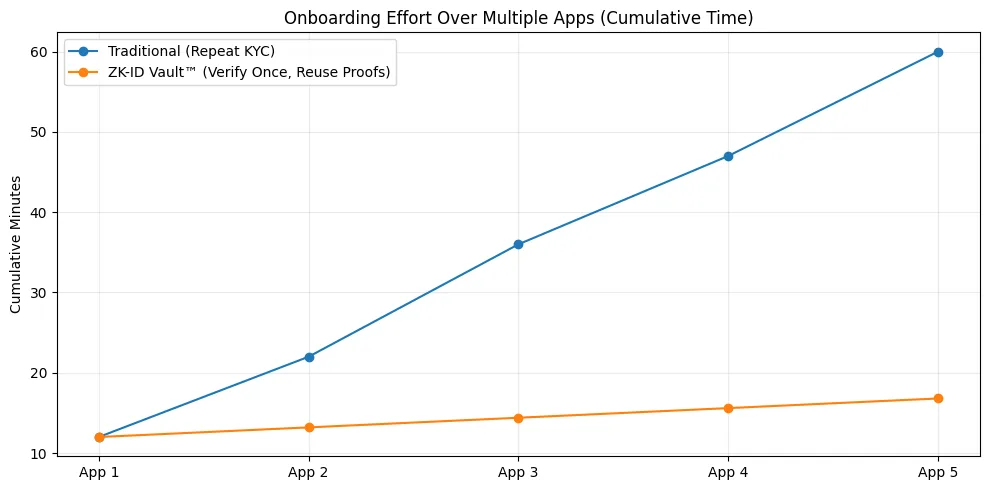
Users who need to prove their identity to multiple platforms can use their existing identity proofs instead of going through KYC processes again. The platform achieves its goal of reducing identity risk through its security measures. The organization does not require any internal storage of confidential information. The established rules create cryptographic indicators which the system uses to execute policy enforcement. The proof system maintains compliance with requirements that compliance teams establish. Users experience a faster onboarding process that provides improved security and better performance capabilities compared to traditional onboarding methods.
Strategic advantages
The zero-knowledge identity layer system decreases KYC expenses by preventing duplicate requests and decreases security risks. The system builds user trust through its function which prevents unnecessary sharing of user information. The system permits access control that uses location data to determine access rights without disclosing exact residency information.
The system provides tiered access models which enable users to access advanced features through demonstration of more powerful credentials instead of providing additional documents. The system maintains protection against Sybil attacks through its methods of preserving user privacy. Platforms can verify uniqueness or credential validity without linking a wallet to a public identity profile. This framework offers essential benefits for governance systems and token distributions and incentive programs.
Risk considerations
Zero-knowledge identity requires trusted issuers and well-designed revocation systems. The system needs performance enhancements to enable users to create proofs on their mobile devices. The organization needs to follow regulatory frameworks which require them to disclose information through established legal channels. The system needs to achieve two objectives, which are to protect user privacy through default settings and to fulfill legal obligations through its design.
Implementation pathway
The first system implementation functions through off-chain operations which use secure verification services while it maintains on-chain attestations to provide transparent results. The system will implement direct on-chain proof verification once both performance and cost conditions permit its use.
The system starts with essential credentials which include KYC confirmation and sanctions clearance and jurisdiction validation. The system base will expand to include advanced credentials which consist of accredited investor status and employment verification.