SlowMist found 472 AI talents that had harmful code in them. This is because hackers are now targeting AI plugins and extensions to get into the devices of Bitcoin investors.
According to a new research from cybersecurity company SlowMist, the official plugin store for the open-source AI agent project OpenClaw has become a target for supply chain poisoning assaults.
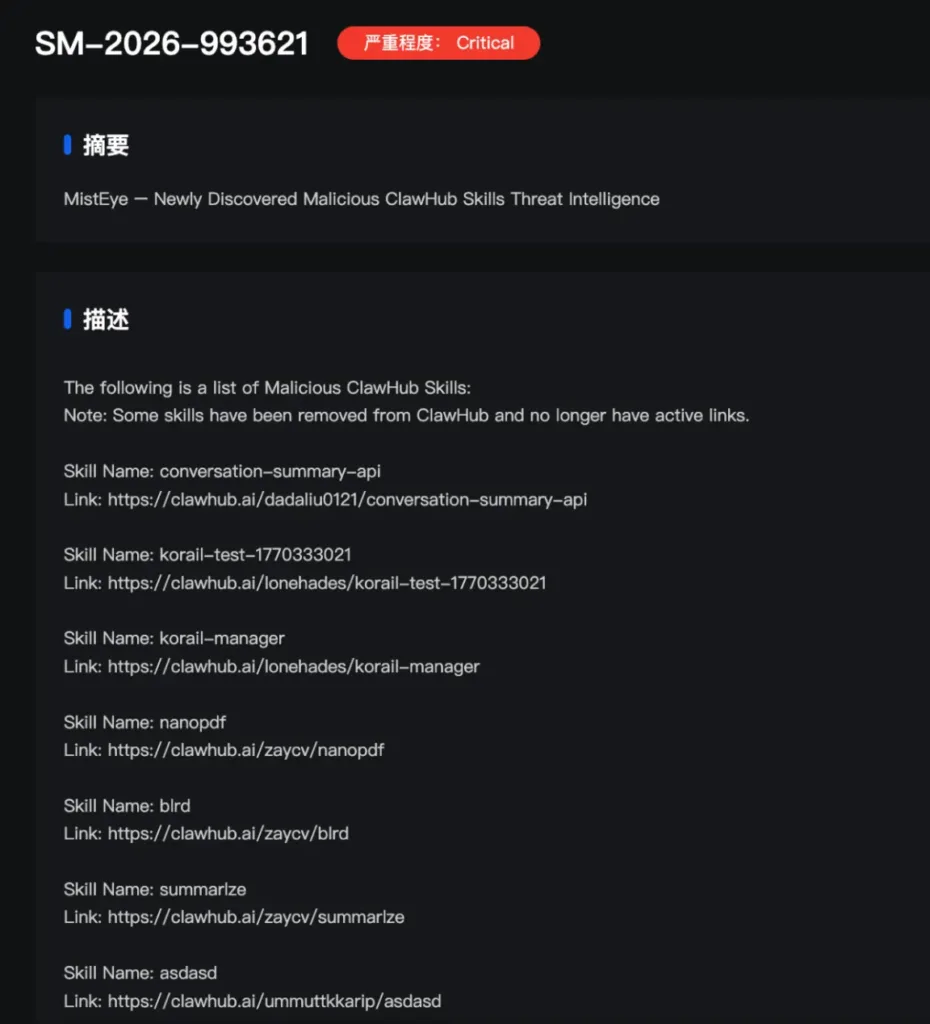
SlowMist stated in a study released on Monday that attackers have been uploading harmful “skills” to OpenClaw’s plugin hub, ClawHub. They did this by taking advantage of what they called poor or nonexistent review systems. The action lets malicious code proliferate to people who install the plugins, which could happen without them knowing the risk.
SlowMist reported that its threat intelligence tool for Web3, MistEye, sent out high-severity alerts about 472 harmful abilities on the platform.
Hackers employ supply chain poisoning to get into a software provider or component and add harmful code before it gets to the end user.
Source: SlowMist
How the malicious skills operate
SlowMist said that the infected skills pretend to be dependent installation packages, which include harmful commands that turn on backdoor functionalities when they are downloaded and run. The business compares this to a Trojan horse.
According to SlowMist, once the malware is installed, the bad guys usually use “extortion following data theft” because the “Base64” backdoor can steal passwords and personal files from compromised machines.
Infrastructure and patterns behind the attacks
Most of the assaults come from the same bad domain name (socifiapp[.]com), which was registered in July 2025, and the same IP address that is used for Poseidon infrastructure exploits.
People often used words related to crypto assets, financial data, and automation tools to describe the bad skills. SlowMist noted that these are the types of things that are more likely to make consumers less careful and more inclined to install quickly.
SlowMist’s findings suggest a more coordinated effort by an organised organization, as numerous affected skills point to the same domains and IP.
This strongly suggests a large-scale attack operation by a group, in which a lot of bad skills share the same domains/IPs and use mostly the same attack methods.
A broader trend across AI extensions
Koi Security, a cybersecurity company, also reported on February 1 that 341 out of the 2,857 AI capabilities they looked at had malicious code. This is a common way for supply chain poisoning attacks to happen through plugins and extensions.
SlowMist suggests that users first check any SKILL.md sources that need to be installed or copied and pasted to avoid falling prey to this threat. Users should also be wary of prompts that ask for system passwords, accessibility rights, or system configuration modifications.